This blog post is authored by Paul Rascagneres with assistance of Martin Lee.
Talos has identified a targeted attacks affecting the Middle East. This campaign contains the following elements, which are described in detail in this article.
This is not the first targeted campaign against the region that uses Dar El-Jaleel decoy documents which we have investigated. However, we have no indication that the previous campaigns are related.
The campaign starts with a VBScript named من داخل حرب ايران السرية في سوريا.vbs ("From inside Iran's secret war in Syria.vbs"). Here are the script contents:
The purpose of this script is to create the second stage PowerShell script described in the next section.
The goal of the generated PowerShell script is to create a Microsoft Office document named Report.doc and to open it.
Here is a screenshot of the Office document:
This document purports to be written by Dar El-Jaleel. Dar El-Jaleel is a publishing and studies house based in Amman, Jordan. This institute is well-known for their research concerning the Palestinian-Israeli conflict and the Sunni-Shia conflict in Iran. Tagged as confidential, the document is an analysis report on Iranian activities within the Syrian civil war.
This document contains a Macro:
The purpose of this Macro in to create a WSF (Windows Script File) file and to execute it.
The created WSF script is the main part of the infection:
The top of the script contains configuration information:
The User-Agent is used to identify the targets. The CC filters network connections based on this string, only allowing through connections made with authorised User-Agent strings.
The first task of the script is to register the infected system by performing an HTTP request to http://office-update[.]services:2095/store. Next, the script executes an infinite loop, attempting to contact the /search URI every 5 seconds in order to download and execute additional payloads.
The WSF script receives payloads of three types, named s0, s1, s2. The payloads are VBScript functions loaded and executed on the fly with the ExecuteGlobal() and GetRef() APIs. The only differences between s0,s1 and s2 type payloads are the number of arguments supplied to the executing function. s0 does not require any arguments, s1 accepts one argument, and s2 two arguments.
The downloaded payload functions are obfuscated, here is an example of the raw data:
The first element is the function type (s0), followed by a separator '-|-'. The second element is the obfuscated function; this consists of ASCII values, separated by '*'. For example the above data decodes as:
During our investigation we received 5 different functions.
During our investigation we received a reconnaissance function a few minutes after the initial compromise. The purpose of the function was to retrieve several pieces of information from the infected system, presumably in order to check if the target is valuable or not (or a sandbox system).
First, the attacker retrieves the disk volume serial number:
Secondly, the payload retrieves any installed anti-virus software:
Thirdly, it obtains the Internet IP address of the infected system by querying ipify.org (the code includes a hint that the attacker previously used wtfismyip.com):
Thirdly, it retrieves the computer name, the username, the Operating System and the architecture:
All these data are sent to the previously mentioned CC using the /is-return URI. The data are stored in the User-Agent separated by "-|-".
Subsequently, we received a second reconnaissance function:
The function acts to list the drives of the infected system and their type (internal drive, usb driver etc.)
In addition to the reconnaissance functions we received 2 functions linked to the persistence of the WSF script. The first script is used to persist, the second is used to clean the infected system. Our machine was served this after taking too much time to send a request to the C2 Presumably the attacker determined we were examining their systems and decided to remove the malware to prevent further analysis:
Finally, we received a pivot function. The function is the only non-s0 function we obtained during our research. This is a s1 function that takes one argument:
Here is the argument:
The purpose is to execute a powershell script:
The PowerShell script executes a second base64 encoded script. The attacker forces the the system to use the 32 bit version of Powershell even if the operating system architecture is 64 bits.
Finally we obtain the last PowerShell script:
The purpose of this script is to download shellcode from 176[.]107[.]185[.]246 IP, to map it in memory and to execute it. The attacker takes many precautions before delivering the shellcode, these will be explained in the next chapter. Unfortunately during our investigation we weren't served the anticipated shellcode.
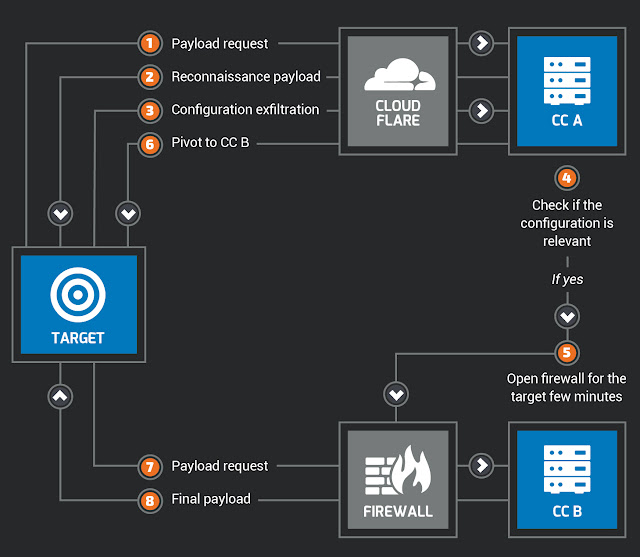
The attacker behind this campaign put a lot of effort into protecting its infrastructure and to avoid leaking code to analysts. The first Command & Control server is protected by CloudFlare. This choice complicates the analysis and tracking of the campaign. Additionally, the attacker filters on the User-Agent; if your web requests do not fit a specific pattern, your request will be ignored. During our analysis the attacker was only active during the morning (Central European Timezone), similarly the various different payloads were only sent during mornings (Central European Time). When an infected system receives the pivot function, the attacker disables their firewall for a few minutes to allow this unique IP to download the shellcode. Afterwards, the server becomes unreachable. Here is a schema of this workflow:
Additionally, we saw that the attackers blacklisted some of our specific User-Agent strings and IP addresses used during our investigation
This high level of OPSEC is exceptional even among presumed state sponsored threat actors...
If you are familiar with Jenxcus (a.k.a. Houdini/H-Worm) you should see some similarities between the VBScript used during this campaign and this well-known malware: usage of the user-agent to exfiltrate data, reconnaissance techniques etc…
We cannot tell if the attacker used a new version of Jenxcus or if this malware served as the inspiration for their own malicious code. The source code of Jenxcus can be easily found on the Internet. However, the adaptation used in this campaign is more advanced: the features/functions are loaded on demand and the initial script does not include all the malicious code unlike Jenxcus.
We can identify different targets based on the User-Agent used by the attacker to identify victims. These are a few examples:
This is not the first time Talos has investigated targeted campaigns using Dar El-Jaleel decoy documents. During 2017, we identified several campaigns using the same decoy documents:
This document is a weekly report about the major events occuring during the 1st week of November 2017, talking about the most important events happening in Jordan, Iraq, Syria, Lebanon, Palestine, Israel, Russia, ISIS and the ongoing Gulf Countries conflict with Qatar.
We encountered this document in campaigns using .NET malware (with the CC: foxlive[.]life) and C++ malware (with the CC: download[.]share2file[.]pro). The purpose of the malwares was to retrieve information relating to the targeted systems and to download an additional payload. Moreover, we identified another campaign using a share2file[.]pro subdomain. Here is the decoy document in this campaign:
This document is a pension list of military personnel dated June 2017, containing names of individuals which we have redacted, alongside a military rank.
We don't know if these campaigns are performed by the same actor or different groups interested in this region. These campaigns are still under investigation.
These campaigns show us that at least one threat actor is interested in and targeting the Middle East. Due to the nature of the decoy documents, we can conclude that the intended targets have an interest in the geopolitical context of the region. The attackers used an analysis report alleged to be written by Dar El-Jaleel, a Jordanian institute specialising in studies of the region. Some of these documents are tagged as confidential.
During the VBS Campaign, we were surprised by the level of OPSEC demonstrated by the attacker and their infrastructure. Legitimate service such as CloudFlare were used to hide malicious activities. Additionally the attacker used user-agent filtering and firewall rules in order to grant access to specific infected systems for only a few minutes in order to deliver shellcode. Following this, the server became unreachable. Another notable observation is the fact that the attacker was active only during the morning (Central European timezone) during our investigation.
The usage of script languages is an interesting approach from the attackers' point of view. These languages are natively available on Windows system, provide a high degree of flexibility, and can easily stay under the radar.
Additional ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as NGFW, NGIPS, and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
VBS Campaign:
Initial script: 15f5aaa71bfa3d62fd558a3e88dd5ba26f7638bf2ac653b8d6b8d54dc7e5926b
Domain #1: office-update[.]services
IP #2: 176[.]107[.]185[.]246
.NET Campaign:
Initial dropper: 4b03bea6817f0d5060a1beb8f6ec2297dc4358199d4d203ba18ddfcca9520b48
.NET #1: d49e9fdfdce1e93615c406ae13ac5f6f68fb7e321ed4f275f328ac8146dd0fc1
.NET #2: e66af059f37bdd35056d1bb6a1ba3695fc5ce333dc96b5a7d7cc9167e32571c5
Domain #1: jo[.]foxlove[.]life
Domain #2: eg[.]foxlove[.]life
Domain #3: fox[.]foxlove[.]life
Campaign #3:
Initial Dropper: af7a4f04435f9b6ba3d8905e4e67cfa19ec5c3c32e9d35937ec0546cce2dd1ff
Payload: 76a9b603f1f901020f65358f1cbf94c1a427d9019f004a99aa8bff1dea01a881
Domain: download[.]share2file[.]pro
Campaign #4:
Initial Dropper: 88e4f306f126ce4f2cd7941cb5d8fcd41bf7d6a54cf01b4a6a4057ed4810d2b6
Payload #1: c5bfb5118a999d21e9f445ad6ccb08eb71bc7bd4de9e88a41be9cf732156c525
Payload #2: 1176642841762b3bc1f401a5987dc55ae4b007367e98740188468642ffbd474e
Domain: update[.]share2file[.]pro
Executive Summary
Talos has identified a targeted attacks affecting the Middle East. This campaign contains the following elements, which are described in detail in this article.
- The use of allegedly confidential decoy documents purported to be written by the Jordanian publishing and research house, Dar El-Jaleel. This institute is known for their research of the Palestinian-Israeli conflict and the Sunni-Shia conflict within Iran.
- The attacker extensively used scripting languages (VBScript, PowerShell, VBA) as part of their attack. These scripts are used to dynamically load and execute VBScript functions retrieved from a Command & Control server.
- The attacker demonstrates excellent operational security (OPSEC). The attacker was particularly careful to camouflage their infrastructure. During our investigation, the attacker deployed several reconnaissance scripts in order to check the validity of victim machine, blocking systems that don't meet their criteria. The attacker uses the reputable CloudFlare system to hide the nature and location of their infrastructure. Additionally, the attacker filters connections based on their User-Agent strings, and only enables their infrastructure for short periods of time before blocking all connections.
This is not the first targeted campaign against the region that uses Dar El-Jaleel decoy documents which we have investigated. However, we have no indication that the previous campaigns are related.
VBS Campaign
Stage 1: VBScript
The campaign starts with a VBScript named من داخل حرب ايران السرية في سوريا.vbs ("From inside Iran's secret war in Syria.vbs"). Here are the script contents:
The purpose of this script is to create the second stage PowerShell script described in the next section.
Stage 2: PowerShell Script
The goal of the generated PowerShell script is to create a Microsoft Office document named Report.doc and to open it.
Stage 3: Office Document With Macros
Here is a screenshot of the Office document:
This document purports to be written by Dar El-Jaleel. Dar El-Jaleel is a publishing and studies house based in Amman, Jordan. This institute is well-known for their research concerning the Palestinian-Israeli conflict and the Sunni-Shia conflict in Iran. Tagged as confidential, the document is an analysis report on Iranian activities within the Syrian civil war.
This document contains a Macro:
The purpose of this Macro in to create a WSF (Windows Script File) file and to execute it.
Stage 4: WSF Script
The created WSF script is the main part of the infection:
The top of the script contains configuration information:
- the hostname of the Command & Control - office-update[.]services,
- the port - 2095,
- the User-Agent - iq.46-|-377312201708161011591678891211899134718141815539111937189811
The User-Agent is used to identify the targets. The CC filters network connections based on this string, only allowing through connections made with authorised User-Agent strings.
The first task of the script is to register the infected system by performing an HTTP request to http://office-update[.]services:2095/store. Next, the script executes an infinite loop, attempting to contact the /search URI every 5 seconds in order to download and execute additional payloads.
Additional Payloads
The WSF script receives payloads of three types, named s0, s1, s2. The payloads are VBScript functions loaded and executed on the fly with the ExecuteGlobal() and GetRef() APIs. The only differences between s0,s1 and s2 type payloads are the number of arguments supplied to the executing function. s0 does not require any arguments, s1 accepts one argument, and s2 two arguments.
The downloaded payload functions are obfuscated, here is an example of the raw data:
The first element is the function type (s0), followed by a separator '-|-'. The second element is the obfuscated function; this consists of ASCII values, separated by '*'. For example the above data decodes as:
- 45: -
- 54: 6
- 53: 5
- 43: +
- 49: 1
- 52: 4
- 56: 8
- 42: *
- 53: 5
- 51: 3
- 53: 5
- 45: -
- 52: 4
- 49: 1
- 56: 8
- 42: *
- -65+148 = 83 -> "S"
- 535-419 = 117 -> "u"
During our investigation we received 5 different functions.
Reconnaissance Functions
During our investigation we received a reconnaissance function a few minutes after the initial compromise. The purpose of the function was to retrieve several pieces of information from the infected system, presumably in order to check if the target is valuable or not (or a sandbox system).
First, the attacker retrieves the disk volume serial number:
Secondly, the payload retrieves any installed anti-virus software:
Thirdly, it obtains the Internet IP address of the infected system by querying ipify.org (the code includes a hint that the attacker previously used wtfismyip.com):
Thirdly, it retrieves the computer name, the username, the Operating System and the architecture:
All these data are sent to the previously mentioned CC using the /is-return URI. The data are stored in the User-Agent separated by "-|-".
Subsequently, we received a second reconnaissance function:
The function acts to list the drives of the infected system and their type (internal drive, usb driver etc.)
Persistence Functions
In addition to the reconnaissance functions we received 2 functions linked to the persistence of the WSF script. The first script is used to persist, the second is used to clean the infected system. Our machine was served this after taking too much time to send a request to the C2 Presumably the attacker determined we were examining their systems and decided to remove the malware to prevent further analysis:
Pivot Function
Finally, we received a pivot function. The function is the only non-s0 function we obtained during our research. This is a s1 function that takes one argument:
Here is the argument:
The purpose is to execute a powershell script:
The PowerShell script executes a second base64 encoded script. The attacker forces the the system to use the 32 bit version of Powershell even if the operating system architecture is 64 bits.
Finally we obtain the last PowerShell script:
The purpose of this script is to download shellcode from 176[.]107[.]185[.]246 IP, to map it in memory and to execute it. The attacker takes many precautions before delivering the shellcode, these will be explained in the next chapter. Unfortunately during our investigation we weren't served the anticipated shellcode.
Attackers OPSEC
The attacker behind this campaign put a lot of effort into protecting its infrastructure and to avoid leaking code to analysts. The first Command & Control server is protected by CloudFlare. This choice complicates the analysis and tracking of the campaign. Additionally, the attacker filters on the User-Agent; if your web requests do not fit a specific pattern, your request will be ignored. During our analysis the attacker was only active during the morning (Central European Timezone), similarly the various different payloads were only sent during mornings (Central European Time). When an infected system receives the pivot function, the attacker disables their firewall for a few minutes to allow this unique IP to download the shellcode. Afterwards, the server becomes unreachable. Here is a schema of this workflow:
Additionally, we saw that the attackers blacklisted some of our specific User-Agent strings and IP addresses used during our investigation
This high level of OPSEC is exceptional even among presumed state sponsored threat actors...
Links with Jenxcus (a.k.a. Houdini/H-Worm)?
If you are familiar with Jenxcus (a.k.a. Houdini/H-Worm) you should see some similarities between the VBScript used during this campaign and this well-known malware: usage of the user-agent to exfiltrate data, reconnaissance techniques etc…
We cannot tell if the attacker used a new version of Jenxcus or if this malware served as the inspiration for their own malicious code. The source code of Jenxcus can be easily found on the Internet. However, the adaptation used in this campaign is more advanced: the features/functions are loaded on demand and the initial script does not include all the malicious code unlike Jenxcus.
Additional Targets
We can identify different targets based on the User-Agent used by the attacker to identify victims. These are a few examples:
c = "U.15.7"
a = "738142201756240710471556115716122461214187935862381799187598"
c = "1X.134"
a = "130427201706151111209123451288122413771234715862388136654339"
c = "Fb-20.9"
a = "585010201750201110021112344661899112271619123139116684543113"
Other Campaigns Using Dar El-Jaleel Decoy Documents
This is not the first time Talos has investigated targeted campaigns using Dar El-Jaleel decoy documents. During 2017, we identified several campaigns using the same decoy documents:
This document is a weekly report about the major events occuring during the 1st week of November 2017, talking about the most important events happening in Jordan, Iraq, Syria, Lebanon, Palestine, Israel, Russia, ISIS and the ongoing Gulf Countries conflict with Qatar.
We encountered this document in campaigns using .NET malware (with the CC: foxlive[.]life) and C++ malware (with the CC: download[.]share2file[.]pro). The purpose of the malwares was to retrieve information relating to the targeted systems and to download an additional payload. Moreover, we identified another campaign using a share2file[.]pro subdomain. Here is the decoy document in this campaign:
This document is a pension list of military personnel dated June 2017, containing names of individuals which we have redacted, alongside a military rank.
We don't know if these campaigns are performed by the same actor or different groups interested in this region. These campaigns are still under investigation.
Conclusion
These campaigns show us that at least one threat actor is interested in and targeting the Middle East. Due to the nature of the decoy documents, we can conclude that the intended targets have an interest in the geopolitical context of the region. The attackers used an analysis report alleged to be written by Dar El-Jaleel, a Jordanian institute specialising in studies of the region. Some of these documents are tagged as confidential.
During the VBS Campaign, we were surprised by the level of OPSEC demonstrated by the attacker and their infrastructure. Legitimate service such as CloudFlare were used to hide malicious activities. Additionally the attacker used user-agent filtering and firewall rules in order to grant access to specific infected systems for only a few minutes in order to deliver shellcode. Following this, the server became unreachable. Another notable observation is the fact that the attacker was active only during the morning (Central European timezone) during our investigation.
The usage of script languages is an interesting approach from the attackers' point of view. These languages are natively available on Windows system, provide a high degree of flexibility, and can easily stay under the radar.
Coverage
Additional ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as NGFW, NGIPS, and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOCs
VBS Campaign:
Initial script: 15f5aaa71bfa3d62fd558a3e88dd5ba26f7638bf2ac653b8d6b8d54dc7e5926b
Domain #1: office-update[.]services
IP #2: 176[.]107[.]185[.]246
.NET Campaign:
Initial dropper: 4b03bea6817f0d5060a1beb8f6ec2297dc4358199d4d203ba18ddfcca9520b48
.NET #1: d49e9fdfdce1e93615c406ae13ac5f6f68fb7e321ed4f275f328ac8146dd0fc1
.NET #2: e66af059f37bdd35056d1bb6a1ba3695fc5ce333dc96b5a7d7cc9167e32571c5
Domain #1: jo[.]foxlove[.]life
Domain #2: eg[.]foxlove[.]life
Domain #3: fox[.]foxlove[.]life
Campaign #3:
Initial Dropper: af7a4f04435f9b6ba3d8905e4e67cfa19ec5c3c32e9d35937ec0546cce2dd1ff
Payload: 76a9b603f1f901020f65358f1cbf94c1a427d9019f004a99aa8bff1dea01a881
Domain: download[.]share2file[.]pro
Campaign #4:
Initial Dropper: 88e4f306f126ce4f2cd7941cb5d8fcd41bf7d6a54cf01b4a6a4057ed4810d2b6
Payload #1: c5bfb5118a999d21e9f445ad6ccb08eb71bc7bd4de9e88a41be9cf732156c525
Payload #2: 1176642841762b3bc1f401a5987dc55ae4b007367e98740188468642ffbd474e
Domain: update[.]share2file[.]pro