Today, as we do every week, Talos is giving you a glimpse into the most prevalent threats we’ve observed this week — covering the dates between Sept. 7 and 14. As with previous roundups, this post isn’t meant to be an in-depth analysis. Instead, we will summarize the threats we’ve observed by highlighting key behavioral characteristics and indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
The most prevalent threats highlighted in this round up are:
- Win.Dropper.Gamarue-6682684-0
Dropper
Gamarue, also known as Andromeda, is a botnet used to spread malware, steal information and perform other ilicit activities, such as click fraud.
- Doc.Downloader.Powload-6681541-0
Downloader
Powload is a malicious document that uses PowerShell to download malware. This campaign is currently distributing the Emotet malware.
- Win.Dropper.Hploki-6682476-0
Dropper
HpLoki is spread via malspam and is designed to steal passwords and user credentials for common programs such as Firefox and Outlook.
- Win.Dropper.Emotet-6681708-0
Dropper
Emotet is a banking trojan with remote access capability that has remained relevant due to its continual evolution to bypass antivirus products.
- Win.Dropper.Kovter-6681669-0
Dropper
Kovter is known for it's fileless persistence mechanism. This family of malware creates several malicious registry entries which store it's malicious code. Kovter is capable of reinfecting a system even if the file system has been cleaned of the infection. Kovter has been used in the past to spread ransomware and click-fraud malware.
- Win.Dropper.Bredolab-6681668-0
Dropper
Bredolab is a trojan with remote access capability that downloads and distributes other malware such as botnets and Remote Access Trojans (RATs).
- Win.Dropper.Johnnie-6681665-0
Dropper
Johnnie, also known as Mikey, is a malware family that focuses on persistence, and is known for its plugin architecture.
- Win.Dropper.Zbot-6681657-0
Dropper
Zbot, also known as Zeus, is a trojan with remote access capability that steals information such as banking credentials using a variety of methods, including key-logging and form-grabbing.
- Doc.Dropper.Valyria-6680534-0
Dropper
Valyria is a malicious Microsoft Word document family that is used to distribute other malware. This campaign is currently spreading Emotet.
- Win.Dropper.Darkkomet-6680876-0
Dropper
DarkKomet is a freeware remote access tool that was released by an independent software developer. It provides the same functionality you would expect from a remote access tool: keylogging, webcam access, microphone access, remote desktop, URL download, program execution, etc.
- Win.Dropper.Ponystealer-6680912-0
Dropper
Ponystealer is known to steal credentials from more than 100 different applications and may also install other malware such as a Remote Access Trojan (RAT).
- Win.Dropper.Tspy-6680869-0
Dropper
The Tspy trojan is used to steal information, such as banking credentials, and installs a remote-access backdoor.
- Win.Dropper.Fareit-6680873-0
Dropper
The Fareit trojan is primarily an information stealer that can download and install other malware.
Threats
Win.Dropper.Gamarue-6682684-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
- Value Name: Hidden
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: Windows Update
- 3749282D282E1E80C56CAE5A
- 65[.]154[.]166[.]201
- 45[.]122[.]138[.]6
- 213[.]180[.]204[.]38
- 46[.]249[.]38[.]155
- 104[.]16[.]19[.]96
- 104[.]16[.]18[.]96
- 104[.]28[.]12[.]17
- 104[.]27[.]133[.]244
- 104[.]31[.]75[.]107
- pafindo[.]me
- www[.]greenfleld[.]com
- safemann[.]tk
- awele[.]duckdns[.]org
- genpral[.]top
- dogged[.]cf
- siyaghasourccing[.]com
- www[.]slompbit[.]xyz
- %AppData%\WindowsUpdate.exe
- %AppData%\pid.txt
- %AppData%\pidloc.txt
- %LocalAppData%\Temp\holdermail.txt
- %LocalAppData%\Temp\holderwb.txt
- %AppData%\D282E1\1E80C5.lck
- \Sys.exe
- %LocalAppData%\Temp\bhvDE00.tmp
- 028fd51a51027132ba29e92e35f1a5c90aad573bcb21c22a919401f53c2e1fe4
- 2234c2a2e7c67e7056c3ffe96476d785917e24c41d4526be48a5aed71008692f
- 2528df691ef2db7f155edf988ad14cf4a60bdd78725ef482731f798ee9bbf22b
- 2e8cf252b1308b94733b3bde811810bf6d4b6ad801cb25ddbe0864cfd2dec75f
- 2e9a6106bf248abadc1d1cca31ea98f49b4b7c790d321ad728c12710ae3dfa16
- 34da76e36056a82a77bb5c498fa7444d57ab471205176d1aff438c4c285764ff
- 388a47dd46aa9d35c2875e687594bd053484d6380f8929d175cb6d4b6b293dcf
- 3a3a6db3d266830cd471cbb84d1707e915bf3ffbe54b84abff5ee703d91e6485
- 4160c38ae1dc75fd8ecadef940a522f123f55d2e7930be952438aa79ec97cfd2
- 4be4c1d3f17092537cbb850c669ec2ef939ca70888b5e8aa334f087833b2e58e
- 62025cd8f7561c4bb148c158b34a7dfa4c167847e6ad1079cd923e9edc759b4a
- 667d6a7d6e36821428d87cab4b4b22acf80e69d4393d7353ef200b0aadd40b39
- 7072e12ef4fedfdc2c015daba59b023b7fe4f9659331939568917178f7354354
- 92a3a24c0cb30f50b9a3e55ed25b913c2a3ebfcce31ed04f5f1c061d2d2463bb
- 9d534c670a3ba061e7582766d5aa26590e7e29a59d71e5c7458141371f04217d
- bb54543651b5e69454f4ec905a7edcfb0c16d9ab6a145d8afd100056bfbd84c9
- c39f50e06a3d18483179c8cb4388b98ae0ba3b78879731c710cf74ed1e423264
- c5c98d6f4a5327dceae54918353096b17205320077347106d3fdcdf8394c4dd8
- c9504878e0f9a6730f2f218b92c458d3e982a78883b601dfba704b724d539e73
- ed3df212bea4cc4c44f7bd39429b15458df0bf7f70caeb4b1b4e1afda0ebbaec
Coverage
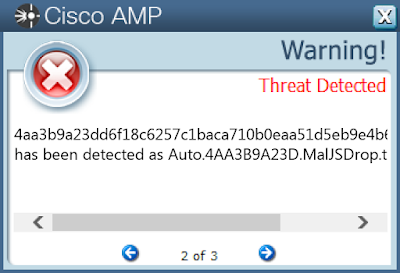
Screenshots of Detection
AMPThreatGrid
Umbrella
Doc.Downloader.Powload-6681541-0
Indicators of Compromise
Registry Keys
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadDecisionReason
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadDecision
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadNetworkName
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadDetectedUrl
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: ErrorControl
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: ImagePath
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: DisplayName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: WOW64
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: ObjectName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: Description
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadDecisionTime
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\66-B3-8A-86-98-63
- Value Name: WpadDecisionReason
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\66-B3-8A-86-98-63
- Value Name: WpadDecisionTime
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\66-B3-8A-86-98-63
- Value Name: WpadDecision
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\66-B3-8A-86-98-63
- Value Name: WpadDetectedUrl
- Global\I98B68E3C
- Global\M98B68E3C
- 74[.]59[.]100[.]124
- 101[.]6[.]34[.]139
- 42[.]114[.]73[.]81
- 186[.]10[.]33[.]220
- 185[.]106[.]208[.]180
- 5[.]61[.]29[.]155
- amniyatgostariranian[.]ir
- %LocalAppData%\Temp\rmfwlhcy.zma.psm1
- %LocalAppData%\Temp\sex1tusl.bnb.ps1
- %UserProfile%\802.exe
- 39b1fb29a067a7129665f1289b608025f2495af0860e3ad903c50b97900556b8
- 42b6c861f47e1fcb5d8afca56545164e81371cc300d54cf8c62c3a6873599c3f
- 6d19edf4fb1031eb9f355b6a769a0a134f62bac5928f7553da1af0cf22eeac2f
- 81ea956fa6739a15975cd95abdb1a7986a7d664dfaa53cbe271a7b5fd1036edb
- a1b3e7b6b3330198ca2cbc5dd8f9a8fc6f7255680629f27c00f552b3982e8770
- a84ead33b515b191683ace1f4fd762a9ab0a47e8a0bdbd141c99042debe16ab5
- ad5fd15f99eedfc43bf9e402569511388e7308bb548b36f2ff3180678c166991
- b7c206428106b9b986e2e72129a94ed77c42cec020f3b2529accd5472de230e1
- bbb2a93d92cdef6cdfb04e8cfb0cb911b07190e3db8aa1a32c93326a8fdb90fc
- c47244459faff7e557ac79b4277b4b8b4bfb550f3d9dbf845af4f352976186c2
- c5ba355f641c33f9197bc6b2fa35e6354ed55e98f476c1fe6dd7a68a07a79016
- e98698880ec4b02325a7b21119783a2841d7c288a2146c73ead369ea749f27bd
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Win.Dropper.Hploki-6682476-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
- <HKCU>\SOFTWARE\Microsoft\Office\15.0\Outlook\Profiles\Outlook\
- <HKCU>\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\
- <HKCU>\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook_2016\
- <HKLM>\SOFTWARE\Wow6432Node\Mozilla\Mozilla Firefox\
- <HKLM>\SOFTWARE\Wow6432Node\Mozilla\Mozilla Thunderbird\
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: LTXD9TT0THZ
- 8-3503835SZBFHHZ
- OQO3TQDA3CDEA0Az
- 216[.]146[.]38[.]70
- 199[.]192[.]21[.]6
- 52[.]7[.]6[.]73
- 192[.]0[.]78[.]24
- 107[.]163[.]140[.]178
- 160[.]124[.]134[.]22
- 64[.]98[.]145[.]30
- 209[.]99[.]64[.]53
- 207[.]148[.]248[.]143
- 31[.]31[.]196[.]52
- 108[.]167[.]133[.]24
- www[.]bvasetro[.]com
- www[.]testci20170903033002[.]net
- www[.]com-logninsauthorize[.]info
- www[.]healinggoodness[.]com
- www[.]losmejorescrm[.]com
- www[.]mytechnik-beratung[.]com
- www[.]vintageontheline[.]com
- www[.]ptt-test[.]com
- www[.]thlg8[.]com
- www[.]mechakawaii[.]com
- www[.]grm-group[.]info
- %AppData%\OQO3TQDA\OQOlog.ini
- %AppData%\OQO3TQDA\OQOlogim.jpeg
- %AppData%\OQO3TQDA\OQOlogrc.ini
- %AppData%\OQO3TQDA\OQOlogri.ini
- %AppData%\OQO3TQDA\OQOlogrv.ini
- %AppData%\OQO3TQDA\OQOlogim.jpeg
- %AppData%\OQO3TQDA\OQOlogrc.ini
- %AppData%\OQO3TQDA\OQOlogri.ini
- %AppData%\OQO3TQDA\OQOlogrv.ini
- %LocalAppData%\Temp\PNj.exe
- %LocalAppData%\Temp\PNj.exe
- \TEMP\Documenti contrattuali.pdf.exe
- %LocalAppData%\Temp\U97.exe
- %LocalAppData%\Temp\U97.exe
- 029a61486c99ab399ea8d1d44f7fcec56160651af33261d6bc024e4179d328e4
- 03b77bb507d1625cba273a703d337218eca7acbf7432df38e9318715deb0ae61
- 0947a945f7aec12d0861b138d80d8a7603167d1cbe775fd6b83d7d94f5ccd444
- 1316a3970c94e825d1d9369a02994c01c1d2f5f28495cb5d8938768c046a2d41
- 1f1a8c28d686b8cea19181f2a54794a4d208c606f9fd0c2e5b5b29609d9d5948
- 1f95c39e22609e5d6009de3caab9224f71efe03ffbbf8bdd1433c71546cb4ba4
- 277ad7f890bbfae3a0e8f24d8fbac51963f4bb161487c095b3f951dc1e0034af
- 2e70ea6467d4fef3c8ec276724fd95c6dd06e7ca5d8fdf4d79732bbcec904326
- 32d89fbd94fe890b7cc07540cdb9c2f2546ec5ee863196a248b4567ae43a07f1
- 32ed5c60cffc9e7b5fe7d740232fdacbd31129e5109fc9db7ff84bb4c07d7898
- 35ac0533eced35b370857e4b2b447e7c24b3224140b60edb5150861c0aa74026
- 394196bc5702741978c1473d0ed835197341a2a30da48130764429fd717f1e74
- 39eebb75f80b28445c50aaf25c1c0c757099bca5393fa4f4c7f5fbcf72588075
- 3b5fe513e2178928fb5f4c07da4cd6e85572332353119c78f276b1aa02008823
- 3bb8174f1cfd068311b93910f975f0422c775b39097fae2a4df0e394dbec4e0a
- 3ef383fac7b7d0a7c41c92c23e56f5301b852c55f797f8642654a489ea891546
- 52ccf4aea5e219eb6d7779f445ef381447eac605db64dc5ad3b28cb0b21f716e
- 539e2b5fcac0cb124b8963df5eb05a9f4246963b7d4b5dd7d1beb10785fffa99
- 56572619ff42dd8a9d58816134605ebf4d08ab4a90972ee5e33b082c9d05e1c3
- 566404b1f32cdf120c82cff12ade5b6ec91056a5058fe76a91d2967973aeb2fa
- 57cecd6a7451c556cb00ac2dcff02a071f29a83b5ec2ee47ef106ec39b9024aa
- 62ffb7c248775b8e6c7f64a093377de2d54c6050063c73486ed3621824068a97
- 665e1b2319553e76b871c4b60cc18b4609334e45fc00309060a98f7b58a0cba2
- 69b312c7ac1509ee9789fb516d6b1d57d1634e5da9831b31f804a3685bf40ed5
- 69d061bace29d55f83505a2ab54ee4fce9cb5f56b8dd666b9dea53b7477adee5
Coverage
Screenshots of Detection
ThreatGridUmbrella
Win.Dropper.Emotet-6681708-0
Indicators of Compromise
Registry Keys
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadDecisionReason
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadDecision
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadNetworkName
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadDetectedUrl
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: ErrorControl
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: ImagePath
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: DisplayName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: WOW64
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: ObjectName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DIMCLOUD
- Value Name: Description
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value Name: WpadDecisionTime
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\88-29-91-6E-18-27
- Value Name: WpadDecisionReason
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\88-29-91-6E-18-27
- Value Name: WpadDecisionTime
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\88-29-91-6E-18-27
- Value Name: WpadDecision
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\88-29-91-6E-18-27
- Value Name: WpadDetectedUrl
- Global\I98B68E3C
- Global\M98B68E3C
- 118[.]189[.]9[.]243
- 207[.]107[.]101[.]210
- 64[.]60[.]82[.]82
- 189[.]222[.]75[.]8
- 92[.]27[.]115[.]15
- 74[.]59[.]100[.]124
- 110[.]10[.]106[.]151
- 172[.]223[.]235[.]13
- 24[.]116[.]40[.]208
- 101[.]6[.]34[.]139
- 198[.]72[.]196[.]89
- N/A
- %WinDir%\SysWOW64\M2uHY39lfNiv.exe
- 05c99bb1cd32c3e0483a8e6a862522918427ef78528c62e0f19bc66d79c61924
- 1685a821c96e8a5238012bdb27727d0ef77337b43a3f42336512e569492385bd
- 196e36f7b92395cb1f1ae8e4abe16bb0d1331cf3964aac1d42e916ded5bd97ac
- 1b6725f6483cf63ff5f553dd1130fbf20ef3dce66f2387e325a0d55ef6357f14
- 27f57d7f6857d965623ca46a8da245449a7bef1f566612c57a5080fb33de61ed
- 2dbff5e59d76080e380afec2a128a2134f4beda7e3871fb82f131fa8dfe23d60
- 533904873f5b44acc5f93353877829ab41e839126d6d5e0b8a7316beac6fe2bf
- 57b5249647e35c906de7c45c196e5768a9b85b0904e348e9ee673957df01bf03
- 5a344865de5fffad1e8c19554146891220a3311580dac74fe6d97b27ef31af0d
- 5dc5976380636bb8944b555547357401e9a6492219afa4b1bf5303910b5c751d
- bd0fdb5024f3b812476319c9542863abad97d80eded9a12012274c76cb24be30
- cab0c315750aa444b838df04fc2506fad7d85cb4c44f823e3ae7e170c940561a
- d668cffa3e3ccf6b216efe3ab24b23d47fe0a5257819216b4a0f0e5ff1ca4aab
- f2c87fa787d18cd3a39d4652f4b567eed206619c62af34b0f37991075044f284
- f560e84bcd29a9454a79a0a90cdd6def36b78d728bad9f2ac41bec75568b1406
Coverage
Screenshots of Detection
AMPThreatGrid
Win.Dropper.Kovter-6681669-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE
- Value Name: DisableOSUpgrade
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUPGRADE
- Value Name: ReservationsAllowed
- <HKLM>\SOFTWARE\WOW6432NODE\XVYG
- Value Name: xedvpa
- <HKCU>\SOFTWARE\XVYG
- Value Name: xedvpa
- <HKLM>\SOFTWARE\WOW6432NODE\XVYG
- Value Name: tbqjcmuct
- <HKCU>\SOFTWARE\XVYG
- Value Name: tbqjcmuct
- <HKCR>\.8CA9D79
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: vrxzdhbyv
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: ssishoff
- <HKLM>\SOFTWARE\WOW6432NODE\XVYG
- Value Name: lujyoqmfl
- <HKCU>\SOFTWARE\XVYG
- Value Name: lujyoqmfl
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
- Value Name: CheckSetting
- <HKLM>\SOFTWARE\WOW6432NODE\47A463C672DD6D6581
- Value Name: 5CFEE7CEF48215E1
- <HKLM>\SOFTWARE\WOW6432NODE\VDZEICWMAK
- Value Name: X6VQZvnwo7
- <HKLM>\SOFTWARE\WOW6432NODE\VDZEICWMAK
- Value Name: ntPgALczv
- <HKCU>\SOFTWARE\XVYG
- Value Name: tnzok
- <HKLM>\SOFTWARE\WOW6432NODE\XVYG
- Value Name: tnzok
- <HKCU>\SOFTWARE\XVYG
- Value Name: usukxpt
- <HKLM>\SOFTWARE\WOW6432NODE\XVYG
- Value Name: usukxpt
- <HKLM>\SOFTWARE\WOW6432NODE\VDZEICWMAK
- Value Name: X6VQZvnwo7
- <HKLM>\SOFTWARE\WOW6432NODE\VDZEICWMAK
- Value Name: ntPgALczv
- <HKLM>\SOFTWARE\WOW6432NODE\XVYG
- Value Name: svdjlvs
- <HKCU>\SOFTWARE\XVYG
- Value Name: svdjlvs
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: fcbburq
- <HKCR>\C3B616\SHELL\OPEN\COMMAND
- B3E8F6F86CDD9D8B
- A83BAA13F950654C
- EA4EC370D1E573DA
- A83BAA13F950654C
- Global\7A7146875A8CDE1E
- B3E8F6F86CDD9D8B
- 78[.]147[.]80[.]55
- 186[.]92[.]100[.]186
- 51[.]77[.]159[.]226
- 54[.]60[.]252[.]133
- 9[.]10[.]183[.]131
- 25[.]171[.]204[.]203
- 200[.]226[.]158[.]165
- 56[.]64[.]211[.]104
- 71[.]17[.]167[.]87
- 71[.]76[.]12[.]139
- 129[.]120[.]185[.]96
- 73[.]221[.]63[.]241
- 89[.]52[.]158[.]17
- 161[.]76[.]36[.]98
- 203[.]56[.]237[.]180
- 110[.]140[.]93[.]114
- 32[.]88[.]113[.]160
- 6[.]206[.]4[.]223
- 31[.]118[.]13[.]79
- 9[.]82[.]17[.]148
- 159[.]113[.]86[.]117
- 220[.]54[.]131[.]35
- 163[.]142[.]40[.]247
- 214[.]212[.]60[.]57
- 131[.]106[.]110[.]95
- 123[.]2[.]250[.]245
- 49[.]160[.]59[.]49
- 114[.]209[.]113[.]187
- 175[.]6[.]48[.]200
- 144[.]14[.]99[.]157
- 182[.]184[.]108[.]63
- 142[.]136[.]194[.]68
- 168[.]78[.]106[.]115
- 143[.]200[.]106[.]175
- 71[.]80[.]198[.]102
- 71[.]20[.]130[.]109
- 43[.]126[.]39[.]85
- 54[.]101[.]217[.]191
- 148[.]251[.]151[.]180
- 153[.]122[.]15[.]46
- 91[.]224[.]24[.]73
- 101[.]47[.]103[.]67
- 150[.]168[.]183[.]66
- 162[.]48[.]140[.]135
- 136[.]32[.]54[.]1
- 14[.]73[.]200[.]171
- 11[.]253[.]136[.]175
- 14[.]64[.]130[.]197
- 114[.]58[.]143[.]28
- 104[.]8[.]80[.]169
- 18[.]49[.]202[.]119
- 44[.]120[.]17[.]31
- 136[.]193[.]247[.]67
- 25[.]68[.]69[.]58
- 84[.]132[.]146[.]243
- 90[.]94[.]24[.]214
- 111[.]167[.]239[.]216
- 205[.]107[.]63[.]68
- 23[.]31[.]134[.]154
- 102[.]95[.]176[.]232
- 219[.]156[.]44[.]255
- 81[.]9[.]242[.]40
- 112[.]58[.]225[.]242
- 1[.]250[.]189[.]144
- 181[.]128[.]105[.]61
- 41[.]132[.]73[.]111
- 115[.]201[.]102[.]188
- 166[.]242[.]22[.]223
- 195[.]130[.]6[.]206
- 16[.]119[.]179[.]29
- 98[.]100[.]170[.]249
- 219[.]215[.]144[.]147
- 56[.]152[.]166[.]131
- 185[.]113[.]241[.]82
- 206[.]163[.]159[.]184
- 21[.]203[.]91[.]206
- 63[.]42[.]236[.]39
- 161[.]234[.]178[.]123
- 123[.]1[.]43[.]230
- 145[.]163[.]125[.]117
- 38[.]89[.]103[.]70
- 121[.]76[.]27[.]206
- 84[.]30[.]50[.]130
- 212[.]67[.]45[.]128
- 181[.]96[.]1[.]34
- 57[.]40[.]56[.]93
- 202[.]89[.]99[.]158
- 18[.]33[.]230[.]2
- 15[.]254[.]97[.]89
- 87[.]134[.]145[.]91
- 99[.]210[.]134[.]76
- 150[.]117[.]58[.]69
- 180[.]71[.]129[.]170
- 45[.]136[.]108[.]51
- 12[.]150[.]168[.]133
- 23[.]253[.]50[.]154
- 102[.]231[.]4[.]10
- 46[.]172[.]214[.]81
- 125[.]22[.]4[.]49
- 124[.]215[.]186[.]198
- 223[.]142[.]72[.]155
- 212[.]205[.]119[.]69
- 153[.]247[.]168[.]105
- 149[.]174[.]138[.]37
- 151[.]232[.]21[.]128
- 21[.]11[.]121[.]107
- 219[.]233[.]148[.]97
- 128[.]198[.]138[.]53
- 96[.]119[.]8[.]208
- 148[.]58[.]214[.]10
- 31[.]190[.]112[.]93
- 60[.]97[.]44[.]10
- 158[.]83[.]234[.]200
- 137[.]40[.]230[.]10
- 215[.]36[.]151[.]2
- 125[.]29[.]217[.]151
- 102[.]51[.]77[.]47
- 110[.]159[.]253[.]93
- 210[.]116[.]166[.]149
- 147[.]240[.]74[.]32
- 53[.]114[.]49[.]104
- 201[.]11[.]100[.]75
- 91[.]49[.]222[.]11
- 5[.]54[.]132[.]49
- 169[.]184[.]190[.]51
- 39[.]189[.]235[.]205
- 111[.]189[.]60[.]176
- 170[.]122[.]170[.]244
- 91[.]202[.]2[.]141
- 70[.]179[.]112[.]71
- 41[.]182[.]103[.]110
- 142[.]14[.]55[.]144
- 73[.]6[.]217[.]29
- 59[.]78[.]136[.]88
- 214[.]117[.]70[.]130
- 154[.]161[.]82[.]126
- 34[.]43[.]14[.]56
- 209[.]160[.]109[.]177
- 217[.]104[.]208[.]153
- 98[.]11[.]81[.]33
- 178[.]246[.]228[.]193
- 150[.]77[.]136[.]244
- 47[.]137[.]143[.]37
- 77[.]196[.]34[.]150
- 6[.]161[.]208[.]50
- 110[.]66[.]55[.]157
- 178[.]28[.]195[.]18
- 91[.]235[.]196[.]78
- 152[.]144[.]194[.]125
- 154[.]238[.]129[.]158
- 143[.]77[.]222[.]58
- 10[.]212[.]55[.]75
- 186[.]208[.]57[.]137
- 191[.]179[.]65[.]236
- 199[.]237[.]148[.]160
- 121[.]225[.]109[.]43
- 162[.]221[.]48[.]127
- 201[.]27[.]166[.]227
- 72[.]92[.]22[.]191
- 218[.]226[.]16[.]9
- 191[.]14[.]127[.]70
- 194[.]149[.]87[.]120
- 112[.]63[.]120[.]198
- 73[.]164[.]233[.]13
- 37[.]180[.]175[.]89
- 133[.]206[.]166[.]246
- 198[.]35[.]115[.]183
- 47[.]167[.]218[.]46
- 135[.]103[.]82[.]205
- 7[.]200[.]105[.]154
- 199[.]93[.]144[.]38
- 59[.]192[.]15[.]15
- 217[.]51[.]139[.]119
- 123[.]127[.]82[.]29
- 78[.]61[.]141[.]7
- 186[.]185[.]52[.]3
- 24[.]199[.]52[.]80
- 5[.]234[.]59[.]44
- 163[.]234[.]185[.]250
- 1[.]252[.]56[.]226
- 187[.]210[.]253[.]198
- 43[.]135[.]189[.]243
- 98[.]148[.]133[.]109
- 88[.]32[.]65[.]1
- 63[.]26[.]72[.]141
- 198[.]69[.]36[.]64
- 66[.]203[.]209[.]140
- 40[.]80[.]9[.]141
- 9[.]194[.]229[.]75
- 103[.]64[.]98[.]245
- 82[.]172[.]33[.]132
- 116[.]245[.]114[.]219
- 107[.]126[.]142[.]41
- 115[.]28[.]249[.]223
- 190[.]208[.]177[.]173
- 135[.]230[.]171[.]152
- 53[.]26[.]51[.]146
- 20[.]229[.]84[.]137
- 124[.]60[.]88[.]212
- 177[.]156[.]53[.]62
- 213[.]167[.]110[.]175
- 88[.]1[.]186[.]185
- 33[.]72[.]73[.]40
- 26[.]57[.]39[.]220
- 71[.]130[.]231[.]34
- 212[.]3[.]115[.]68
- 201[.]163[.]21[.]128
- 33[.]65[.]249[.]104
- 74[.]63[.]38[.]62
- 163[.]14[.]66[.]71
- 91[.]213[.]237[.]149
- 28[.]10[.]105[.]191
- 222[.]21[.]121[.]112
- 78[.]228[.]61[.]65
- 42[.]132[.]214[.]17
- 136[.]80[.]39[.]220
- 32[.]127[.]135[.]111
- 132[.]241[.]123[.]26
- 122[.]117[.]211[.]198
- 165[.]184[.]216[.]139
- 1[.]50[.]235[.]118
- 76[.]221[.]33[.]248
- 141[.]233[.]254[.]233
- 197[.]27[.]162[.]130
- 223[.]239[.]79[.]7
- 15[.]253[.]169[.]20
- 155[.]29[.]149[.]82
- 142[.]12[.]122[.]234
- 209[.]144[.]118[.]213
- 58[.]213[.]179[.]16
- 175[.]3[.]47[.]242
- 39[.]40[.]132[.]64
- 106[.]162[.]109[.]12
- 195[.]142[.]187[.]29
- 209[.]172[.]146[.]111
- 173[.]228[.]9[.]90
- 40[.]121[.]144[.]40
- 211[.]67[.]42[.]241
- 160[.]110[.]143[.]245
- 120[.]31[.]29[.]140
- 8[.]65[.]254[.]19
- 86[.]205[.]253[.]167
- 110[.]157[.]4[.]220
- 75[.]59[.]231[.]248
- 208[.]61[.]5[.]175
- 144[.]31[.]70[.]99
- 117[.]37[.]13[.]214
- 51[.]217[.]73[.]162
- 182[.]223[.]166[.]190
- 207[.]57[.]189[.]34
- 17[.]27[.]53[.]89
- 136[.]219[.]235[.]153
- 67[.]143[.]237[.]178
- 165[.]188[.]89[.]101
- 122[.]214[.]248[.]8
- 158[.]237[.]30[.]116
- 41[.]192[.]242[.]157
- bscw[.]paritaet[.]net
- www[.]dso[.]pl
- %LocalAppData%\4dd3cc\519d0f.bat
- %LocalAppData%\4dd3cc\8e9866.8ca9d79
- %LocalAppData%\4dd3cc\d95adb.lnk
- %AppData%\b08d66\0b3c0b.8ca9d79
- %LocalAppData%\Temp\~DF5BCE8BF7EE69B404.TMP
- %LocalAppData%\Temp\g1b14dab.rdk.ps1
- %LocalAppData%\Temp\pey0h1im.c1n.psm1
- 044be48174fa81edefd3b35843d76998c4a72defd3fb0b7e0b5ecaa7d205c71d
- 20998f4c46d0da1403bf6d894fd0396432cefa7b544fab1929be314f5c710e94
- 26ad68daec330f0af6a5455a2293a1cdba9b9e9ca025b3d733e59d1c2cd6a3f6
- 27b93d841df9dfe56d07a1430d1ab1bb88e8dea3e413b1ad8d27276a14cb298d
- 29bb23883b4cc5f4789114445bb397d19ded701c6e0dc80b5d946d5a2b54a027
- 30ebdae089ff27b5a6ef838ca17597f4d0728b25dcc34c59aafc997fce3c84a4
- 3bbfbf7b816f5afb26a04d040b911a0efa58bde3770f45735b991d69af23eba2
- 3be48068d2d627fafa15cdd22e1199206884b943622c98c4f8071d5e610a5498
- 458ba8a48200ae6c90c3789427dec37078531978a91730f153f2399aad5cd6b3
- 47f74240978d492d091790fab667d39b2c6e42e86d29a983e6e6dac0b62875c5
- 4aa3b9a23dd6f18c6257c1baca710b0eaa51d5eb9e4b66fbc0731d755cce67dd
- 4f1aa4b14e4c59ff2d9f1e4905e5e246b751246f164a1d7d1edd54ce4007cc81
- 5d8a4cdc70c0dd0b373f1a50c140622772f6590a31c697e0cf1dd9b89b7e6cc6
- 654e000b1c469894355614e418f9d47246fbb9a0184627cd71270f3091c8a9e8
- 6ec77a1190da50078315a9e4f9370f2ebee86eedf4e405ab11d29ac7ca196c64
- 86a095ae381129b0f0b1fc48f9e9cb8f264bbdb9538aa2db50c82555f36f5943
- 89985343060c86a350986e14a31cdbfcd88b7858dd098fb50668717bf5479b76
- 940b8b2d4c5e160f7072e05957f08446d889027a80e671400441edf0751f6285
- 9c3213ffa67c205a8f0d172dcf9dafb0f57f4f81ad3f3a134955f184237c0ad8
- 9fd19c951d381be78083e0dbcbe19b2f8aa342697b4daeeabd477d92beaea7e3
- a34ef5a0bb557ec591b1f75ad280bd4fd3cd34ff9a443e6f1f5fc72810852e86
- abb2228d2d252c4722b978492c029930fb0e4882b349a3b82506554666476b25
- cd4ca0a0e849e7210825f6ae9363b672787aa750078f4ec319b8dd00790ab25d
- d0ee281046421afc2dc25081d14b2643914f12c4ad753fa382b1c16f8fca13ae
- d29e129b708074f8f7dc8965119c9ea4ea314f49568b99ccf77bb1014bdacb41
Coverage
Screenshots of Detection
AMPThreatGrid
Win.Dropper.Bredolab-6681668-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: HKLM
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: HKCU
- <HKCU>\SOFTWARE\CYBER
- Value Name: FirstExecution
- <HKCU>\SOFTWARE\CYBER
- Value Name: NewIdentification
- <HKCU>\SOFTWARE\CYBER
- Value Name: NewGroup
- Administrator1
- Administrator4
- Administrator5
- 212[.]52[.]43[.]195
- 52[.]8[.]126[.]80
- tanne0214[.]zapto[.]org
- remotes[.]no-ip[.]biz
- 7896[.]sytes[.]net
- imacdrake[.]no-ip[.]org
- creditoshabbo[.]hopto[.]org
- humberto1992[.]zapto[.]org
- ereticus1[.]no-ip[.]org
- %LocalAppData%\Temp\Administrator2.txt
- %LocalAppData%\Temp\Administrator2.txt
- %LocalAppData%\Temp\Administrator7
- %LocalAppData%\Temp\Administrator8
- %LocalAppData%\Temp\Administrator7
- %LocalAppData%\Temp\Administrator8
- %LocalAppData%\Temp\Administrator2.txt
- %LocalAppData%\Temp\Administrator7
- %LocalAppData%\Temp\Administrator8
- %AppData%\Administratorlog.dat
- %WinDir%\SysWOW64\WinDir\Svchost.exe
- %WinDir%\SysWOW64\WinDir\Svchost.exe
- 48180ade1a05ee5c2110ee4c71754da73383cd4819289c6c091d519855f1627f
- 56cc8bd6718775c3b9de1bf381824d1bdc9a15b6b9c9e056e2ed3d93c6e731ec
- 5db46724856b56cd131601c4e5c39e006c47408b9a5be64fd8d7a8126e402607
- 87e20d484f20fe2e21152d74f8a8cbd145c2bfbd501932c23d7be394cf1801e5
- 94986d91cb3d0f3de612a63b4d7e9ad005dab44a05e895499a9cd5e8baa544c8
- 987b509f8ac3f8cf96c5ea2060b1d6026e3ead908168728bd602f00f4a4b73ff
- bcc49772a1699a5f2858f85f098fabc1adcd8ebb8834d806ddb23509c83c5e4a
- cb397ef75dbf1a3cd2269e209dfb70d1a1910ca2a437d010b2c0a11a3a9dd740
- e1feb2a427d5f5e40e3b9840f4f1795bb775e1bfbcf0f4d4f7df8a09a4ab0cff
- e5fce427ec167c53e5b34873596a72ce348a02d578d0951fa22d59b590dd0ebb
- f095a1ae871884b632eb885dd80c9c3d27079abae8c8daa8237b48df41708f5d
- f80624e00b65c0560fd5da5834e4539740d7ac19872c10389dfbee7b1d46cefa
Coverage
Screenshots of Detection
AMPThreatGrid
Win.Dropper.Johnnie-6681665-0
Indicators of Compromise
Registry Keys
- <HKLM>\Software\Wow6432Node\Microsoft\MediaPlayer\Preferences\
- <HKCU>\Software\Microsoft\MediaPlayer\Preferences\ProxySettings\HTTP
- <HKCU>\Software\Microsoft\MediaPlayer\Preferences\ProxySettings\RTSP
- <HKCU>\Software\Microsoft\MediaPlayer\Player\Tasks\NowPlaying\
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: Video Display Driver
- <HKCU>\SOFTWARE\DN-AKFCC
- Value Name: ServerStarted
- <HKCU>\SOFTWARE\DN-AKFCC
- Value Name: InstalledServer
- <HKCU>\SOFTWARE\CROSSFIRE
- Value Name: NewIdentification
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
- Value Name: Isass
- <HKCU>\SOFTWARE\LAMMER
- Value Name: FirstExecution
- <HKCU>\SOFTWARE\LAMMER
- Value Name: NewIdentification
- <HKCU>\SOFTWARE\CROSSFIRE
- Value Name: FirstExecution
- _SHuassist.mtx
- _x_X_BLOCKMOUSE_X_x_
- _x_X_PASSWORDLIST_X_x_
- _x_X_UPDATE_X_x_
- sr54g65dg45ds5s8798ae
- sr54g65dg45ds5s8798ae_PERSIST
- XTREMEUPDATE
- dN-AKfcC
- dN-AKfcCPERSIST
- sr54g65dg45ds5s8798ae_SAIR
- dN-AKfcCEXIT
- Isass
- Isass_PERSIST
- Global\2fbe6fe1-b6df-11e8-8419-00501e3ae7b5
- Isass_SAIR
- 187[.]59[.]175[.]44
- 186[.]237[.]232[.]135
- 177[.]17[.]90[.]164
- 177[.]206[.]100[.]238
- 186[.]237[.]232[.]88
- 177[.]125[.]230[.]242
- 141[.]255[.]144[.]44
- codelux2017[.]ddns[.]net
- skypeprocesshost[.]ddns[.]com[.]br
- homersides[.]duckdns[.]org
- ducklife[.]ddns[.]net
- wandersongay[.]ddns[.]net
- %LocalAppData%\Temp\XX--XX--XX.txt
- %WinDir%\Root\Video Display Driver.exe
- %LocalAppData%\Temp\XX--XX--XX.txt
- %WinDir%\Root\Video Display Driver.exe
- %WinDir%\SysWOW64\hi-IM\csrss.exe
- %WinDir%\SysWOW64\hi-IM\csrss.exe
- %LocalAppData%\Temp\UuU.uUu
- %LocalAppData%\Temp\XxX.xXx
- %LocalAppData%\Temp\UuU.uUu
- %LocalAppData%\Temp\XxX.xXx
- %LocalAppData%\Temp\UuU.uUu
- %LocalAppData%\Temp\XX--XX--XX.txt
- %LocalAppData%\Temp\XxX.xXx
- %WinDir%\SysWOW64\Isass.exe
- %WinDir%\SysWOW64\Isass.exe
- %LocalAppData%\Temp\XX--XX--XX.txt
- %WinDir%\Root\Video Display Driver.exe
- 04c42d576ba4b5ca2cc45462c75352276aed4a6a678f2b75c0157a20e7421d86
- 0c7c3f4f67e67df34376b41b8bd98973c874d034cb2ae85184b03b9211dc56be
- 182311866d129d6203d9bd8f139b92ce7b55cdd691c6694f43553edcd59f9ddd
- 226a1ad2b6aca583e340057cfc9c8e638fecb935ef34ef262ee067eb0aa54c16
- 322fac0e1a6069a7b98f6fd5a30734cf73072084cf6529bc746f238a88907418
- 44364855cb08ace848e4911bfe857787b48e7c8ef004f39c983962d10b162477
- 5af2fbf37c77c3ff9228059325f203f7252363862480b65242e6952fc61f0c73
- 87aecc8838b2d8f6e169950ad621932ba2d10106fae3681140e04c7ae43661c4
- a6086ddbbeaa39e13d4cb807642ee1080b768314a67015941547af7361a80e97
- b3f9905c476ecf22dacd1d15e6ff5425933662dd297685dc475128907c96e705
- b67f0572957a4f71ec4afe43a7647d43044a23554a099735a3b99d910bc24867
- c84c2e49fc9b57e1e53c91ee35bf0a85106582211dd544326d1e10cdc3a29218
- d4d77eae0d0481baa2313aa84775a1906687c8e948d1e1b52b2d8ea74430e169
- e524f71e112623370be56536226766338a308f77e6a042937d471d5244047f3b
- ed684ccd44e82e65b2563ce6c7d8e5d48560fb98e7cc42bf483707b18c52efba
Coverage
Screenshots of Detection
AMPThreatGrid
Win.Dropper.Zbot-6681657-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\PRIVACY
- Value Name: CleanCookies
- <HKCU>\SOFTWARE\MICROSOFT\AHPYE
- Value Name: Toitqa
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: {913237A3-A7F1-4D42-F774-A9CF00C8A7BB}
- <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
- <HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
- Value Name: CheckSetting
- Global\{FA015A2D-CA7F-2671-F774-A9CF00C8A7BB}
- Local\{93231DB1-8DE3-4F53-F774-A9CF00C8A7BB}
- N/A
- grandesupport[.]biz
- N/A
- 39784419d8565a3ced22083127a61835770f3bc638f87b3ea9318ffcbfdaf848
- 4017493d29c4951897f50c9e237c6eeb194fb7899f9203975a93a7c11c2368c7
- 51617fde592532fac1020fc924adc6d15be9bab516ec3d36e8910f7406123476
- 683d10e142f3a87561e1fd84881079c716792add73d26bb647c2bad37efb7492
- 786c00b22f4337b0745fa9614a2810258e214bf4f61f36a8cf9a6a08647d15c6
- 796e89fe89692a2d27fd8645fc215df4bab2ee992f6f1660b1790fbdf11b31a6
- 7b1aa81187bb675440e409c2a0572804abad624c1a7c446831ffc619c14c447a
- 88e7defd3c756d2d34e43c2988c1d650f55167c4c8649010c6b21d0537f968c5
- 8b3b86c5fd43a44f09424eb36f0a849c0617d11dc1f8b3d60c9c4734fcd8a7ff
- afb294c4d70a0cc8364963c3671ee65e176c26d367201bf6063ef3e2ae200b0a
- d2a4c371dd2aad5d29909117c858e22996f0da89b5bbac232be3b36ff881ce97
- dac1c6f00041fc055ef9a091156116a62633d8e986fdc7fc56e9bd5f88ef3ea1
- fa0bede1310a0cf7f146bc659c89cf815725c5984de50748ff77d9f0d693b1dc
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Doc.Dropper.Valyria-6680534-0
Indicators of Compromise
Registry Keys
- N/A
- Global\552FFA80-3393-423d-8671-7BA046BB5906
- 173[.]201[.]185[.]6
- 103[.]27[.]232[.]26
- 104[.]236[.]33[.]143
- 184[.]168[.]188[.]1
- 91[.]216[.]107[.]152
- fithealthyliving[.]net
- staging-geblog[.]b2ldigitalprojects[.]com
- arcbko[.]com
- wcspl[.]org
- bechner[.]com
- %LocalAppData%\Temp\538.exe
- %LocalAppData%\Temp\kg4a5d2p.1ae.ps1
- %LocalAppData%\Temp\vknsrz3n.wpf.psm1
- 0238239e3cf2075650f629cb689f505107bda604df0aa2574db2a53600022f38
- 069ff6dca25b828171a73beb093055320d309bc9143a1ae5b540465c655192c4
- 242aae6952657369293d30dc1d3764b6966ac1a6e6d62e969f00d19a9fb7b193
- 301a228cf13e759f90b0a3feed41dff781c7f85e8b605790912ccb44d473d572
- 45dea266a99e322ccedab4a3896b2861f494690db67f6e02132a7b8b4b5a89e7
- 54f695dc4f5498b1b04287dbe71674273a3252e0f18e924b8acd8909f33c7caa
- 5941d8a04f73dbe37dda523049e58c5973f0c4ae41662697f11d7e345798b9dc
- 5f7de3a70448c1e1285bd53c5109cbd07f2c06b95acedd9b983917ff033f209b
- 7af1f7a16f09716615b2d6de7da9f741a69dd9d9709284b83ca177972ab7a7e7
- 7b86ed501d87008bdce4d834b7785fe819abf0aa1a57e8d8c3375bbd5305f6c8
- 7fcf47adafd831ba002e265e38de3b65b0323f9c25c79f976112fb057029d450
- 874ec93d6dfd58dc22c195e10b7da0a105accbcd3c89ce88455c17b1f277145d
- 91e151742255613156ff2f026af1fb0c1c1414fcac566994c52c4d3072d42e64
- a8c0129de81bf9bd7ea0a8f27fab96b798a60a98655c9137a0425f6dd3e9b295
- afd149d4cccd6600794a46652cea139c70f3d4961e5b501d66854b9f9ea91b75
- b6f2936958c9133e87ae4c0acb73265514e460959438b175648e17ba7818fbbc
- b8f79a3b73aeb5c6e075a4ae6bc921397eccc9a99589b37e2c0a6d98ef3c5ea2
- bf1c5f995535d59a70d970f9892a57d2f309b9076787199a1af221e9f8284527
- c176225326d983a4698f5b12e8c17f4efff2f1d025148570725abee3cbef5af0
- cfe5248f7c852dc86994b44fabb8415e864a8b27805acf844af8533c40c17896
- efa9962b68e9090b2fa71ee3b22726715a9d2c65d223f2fdcbcc24b621806a12
- f520f9cc0e7e736664ac1409931351a3b37331b84f9a1d845f7a279963db906a
- f604290550ccfa8be31f5c14078b4b1b95e93778b0d75e5284a3515ca160b49d
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Win.Dropper.Darkkomet-6680876-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\DC3_FEXEC
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: turnon
- YG75FBKJ76
- 91[.]200[.]124[.]201
- val[.]myftp[.]org
- %AppData%\dclogs
- %AppData%\ace.exe
- %LocalAppData%\Temp\OSXEF.txt
- %LocalAppData%\Temp\OSXEF.bat
- 03c483310dd297d66e6d5a6638267688b056a5d5b21b667bba8b7a9ab664889c
- 07e3f9989a69d60372e72b8f25bb82c3a40eb5b10b7d33d0a296b392ba9c5135
- 0a00f60a8af2d9f32a08376c10f7f624438494aa9213f81f395b3d8f3a1eb65a
- 0c03079c94b8d104f8056011b896e388166697bae717de5a4fa31f4638e9381f
- 0d9d0c68de0c21b6c1a800ec3985a2986d88869eb334ab1c6dc0c5dc40119483
- 0e0b5874acbca1fba6f98c9a30ae1505a1a87e6368a8906a6a6fd8e28bb31427
- 0e2827de18a187c5ed31e9dcf44ca4f3f407f16a4e6f6a7b01304494514592da
- 0f06f2ab0ce310049915962b7961b58b46bca4beba857633ac95b2a13cfa5d05
- 0f99f662e7bab77cc78547802cdf85d810ce971682f7b50bdb8c77fcbc85aaaa
- 1119d8e1bdd4bdf582a4d8047835bdd5f1fa2bc0f5f39f7e9ddc6421ffd9feb4
- 12883e0f1911daadb66fbbb66b7be9feb6e02a1c3447445ce1947dd6fc600410
- 14c7eaa26712518b9d8c811cc160a127aa3ef2f19d0f7da38549aadbcbc6b38e
- 169fe2cad2ab1c592d1e573f4d8d108d1cb842219a1078cfd0bb82cb4419f66d
- 1744294b2eea0b04f59090a13d0a03796498bc303cae65b04129652b8a5b8cd6
- 179f922f65f7437dc74ab133bd47f4d463cb703cf63dafc59ed4611eef7eb3ac
- 1992cad7397af3479dfd7945ff7d12c0abcee4311f043b026eb41172898b1a7d
- 1a05832ebb6c608346f01306db48b0afd4e571b06d9a7c5c2845d7aed1f7d207
- 1ca18752e5cb2d58ee1de63b9402993558560eff0592930b281a083d1a635f17
- 1e14c8f6b9c81c69aebdd5253527534d819474c41fa0be9c7edfe17e543baa17
- 1e2bffa2672a47cdbfd0dfd9f4a531ef5e1c654ee3c262fd21b4fb22630c032e
- 1e4a660328cf9d5332b4aab97933ed451af7c8925ad8550b7678c9c3c522c71a
- 236d1f514cf2f46d4833377df1b854830990f723d0599659c0c938cdafb1e754
- 2401a683279fd61dffdb81d4f0a946fc129bc72d5c5e8061303323f74d3e19a5
- 276e71bebd8336e347e3ed2cbe2787a1de99cefa706af48feeccf3395e3219a3
- 28252e1df5f42535c404992c9e65c6c165c938d0c7d9e7062ce06ee4ba42cbb5
Coverage
Screenshots of Detection
ThreatGridWin.Dropper.Ponystealer-6680912-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
- Value Name: Registry Key Name
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
- <HKCU>\SOFTWARE\Microsoft\Office\15.0\Outlook\Profiles\Outlook\
- <HKCU>\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\
- <HKCU>\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook_2016\
- <HKLM>\SOFTWARE\Wow6432Node\Mozilla\Mozilla Firefox\
- <HKLM>\SOFTWARE\Wow6432Node\Mozilla\Mozilla Thunderbird\
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
- Value Name: MPX0O4RP3X
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
- Value Name: LTWTXJJ0
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: K62XHZYXTH
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
- Value Name: XTWXCZIXDHF
- 8-3503835SZBFHHZ
- 299N2C3FD0EVCX9z
- 47[.]91[.]170[.]222
- 185[.]230[.]61[.]161
- 52[.]5[.]251[.]20
- 198[.]54[.]117[.]200
- 209[.]99[.]40[.]222
- 104[.]27[.]140[.]60
- 185[.]207[.]8[.]246
- 146[.]196[.]82[.]3
- 172[.]217[.]10[.]115
- 221[.]246[.]80[.]218
- 47[.]254[.]67[.]48
- 180[.]76[.]97[.]209
- 209[.]99[.]40[.]223
- 158[.]85[.]87[.]76
- 182[.]237[.]0[.]67
- 35[.]194[.]164[.]137
- 104[.]149[.]211[.]146
- 104[.]28[.]8[.]192
- 107[.]173[.]131[.]73
- 103[.]224[.]182[.]243
- 52[.]78[.]124[.]149
- 199[.]192[.]25[.]192
- 208[.]91[.]197[.]132
- 209[.]200[.]154[.]54
- 198[.]185[.]159[.]144
- 203[.]170[.]80[.]250
- 176[.]9[.]3[.]251
- 50[.]63[.]202[.]69
- 208[.]91[.]197[.]46
- 183[.]90[.]253[.]13
- 52[.]7[.]6[.]73
- 192[.]0[.]78[.]24
- 182[.]61[.]117[.]253
- 198[.]54[.]117[.]218
- 34[.]240[.]216[.]169
- 198[.]57[.]247[.]216
- 216[.]239[.]32[.]21
- 91[.]184[.]0[.]14
- 216[.]239[.]34[.]21
- 104[.]28[.]9[.]192
- 23[.]238[.]221[.]30
- 67[.]222[.]38[.]88
- 50[.]63[.]202[.]89
- 104[.]217[.]9[.]112
- 208[.]91[.]197[.]91
- 185[.]53[.]179[.]29
- www[.]841bifa[.]com
- www[.]n*****boutique[.]com (Editor's note: This URL has been censored to remove offensive language.)
- www[.]goedutravel[.]com
- www[.]xctljc[.]com
- www[.]redkoe-porno[.]info
- www[.]femalesdress[.]com
- www[.]planeggerstrasse[.]info
- www[.]qfs[.]ink
- www[.]funnysworld[.]com
- www[.]xn--vuqu93jrjhqkc[.]net
- www[.]suatusta[.]com
- www[.]casineuros[.]com
- www[.]rabe-networks[.]com
- www[.]reducetarian[.]biz
- www[.]selviproperty[.]com
- www[.]giftedaroundtheworld[.]com
- www[.]aditsachde[.]com
- www[.]oane4[.]win
- www[.]ayursanskar[.]biz
- www[.]benthanh-toyota[.]com
- www[.]puptowngirl[.]net
- www[.]cyn[.]ink
- www[.]theniftyfiftiesband[.]com
- www[.]webbyen[.]com
- www[.]globaltimbereurope[.]com
- www[.]3zci3b[.]info
- www[.]xn--fjqu42jgii[.]com
- www[.]mizukusahonpomeibi[.]com
- www[.]zjjdmd[.]com
- www[.]donghairc[.]com
- www[.]theadvancedcoach[.]com
- www[.]telegraphresidences[.]com
- www[.]sjckt888[.]com
- www[.]schmidtatlanguage[.]com
- www[.]vdemg[.]info
- www[.]happyslider[.]com
- www[.]chfnik[.]com
- www[.]crstudents[.]net
- www[.]fiveroot[.]com
- www[.]luxuryconversion[.]com
- www[.]studio51[.]style
- www[.]custombusinessapps[.]net
- www[.]verzuimverzekering[.]info
- www[.]float2fit[.]com
- www[.]ketones[.]info
- www[.]dk-drugs[.]com
- www[.]reviewhqs[.]com
- www[.]revivemyappliance[.]com
- www[.]scgcgg[.]com
- www[.]mjkrol[.]com
- www[.]bigmovephilly[.]com
- www[.]chinaxzl[.]com
- www[.]thienduonghoaviet[.]com
- www[.]rsstatic[.]com
- www[.]fattoupdates[.]date
- %LocalAppData%\Temp\subfolder\filename.vbs
- %LocalAppData%\Temp\subfolder\filename.bat
- %AppData%\299N2C3F\299log.ini
- %AppData%\299N2C3F\299logim.jpeg
- %AppData%\299N2C3F\299logrc.ini
- %AppData%\299N2C3F\299logri.ini
- %AppData%\299N2C3F\299logrv.ini
- %LocalAppData%\Temp\Bfz8hctw\msltqlrvah.exe
- %WinDir%\SysWOW64\shdocvw.dll
- %ProgramFiles% (x86)\Ktbchzlcx\winnnhlg.exe
- %ProgramFiles% (x86)\Copx0\services9rdh.exe
- %ProgramFiles% (x86)\Copx0\services9rdh.exe
- 0e5a451852c815706a150befb73bdc405dc598a78b2e7dc63b35f520004feca6
- 1f422318d70cdf15e6d1063be1bd7b169b664f6f1be0ca16aa9056d8c8f66ab1
- 2e8f73a03161b25c97679b7355216ba238dbac83606f0167d0e37555c45c8805
- 714dae6f00f1111c8b1df7028b2a42f1ba1de8c04c1daf312705ca681e4cb50c
- 7ee3c73197123364b96ae7049659349cc23814205c5694ffa4d4bd5e549100b7
- 8e501cd8772aa05320f248a288288803399c0a066ac0b72f4964b535bdbce9a5
- ad73ee11fd4721805d0f59f6946d66a9cd3168a5653fbb3af1169f5085af2c43
- c69593cb3f3af2548ad6acdc58771ff9106b9159ca335f33dfac742e6c5645d4
- d4cfe9a0b6a7b4c18a29432b0af83ced8e25598be1b40f28ff653663c9e03c49
- e499b206363260d823bcb8132ba6557facc614ad579cbfce2a198d6b1e1a7643
- eafe32cbdf7df2612b5d72e2ffbff2efd98908d8356d81ee4cc55899b3252dd1
Coverage
Screenshots of Detection
ThreatGridUmbrella
Win.Dropper.Tspy-6680869-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\REMCOS-4TJ61G
- Value Name: exepath
- <HKCU>\SOFTWARE\REMCOS-4TJ61G
- Value Name: lic
- 3749282D282E1E80C56CAE5A
- Remcos-4TJ61G
- Remcos_Mutex_Inj
- 89[.]38[.]241[.]133
- 173[.]46[.]85[.]220
- novachim[.]ro
- doublelogs[.]ddns[.]me
- %AppData%\D282E1\1E80C5.lck
- %AppData%\jeje\mula.exe
- %AppData%\jeje\mula.exe:ZoneIdentifier
- %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\jeje.vbs
- %AppData%\oir\jjd.dat
- 2f416035e7d2527d7ab1bae1a5a03cfeaa87f1bbe5e580e903510c9fe61be0a9
- 45f3dd601882ceb313fc33e19353e0bac78736c4817e9bde21a5b2635d3967e1
- 4fdde7b1b995d53e924f9afb20235ef20fdfeb6c725bbc8a471f2ed3fb7e2767
- 5e6b55f97481c9bb254d22af75fdeca2b9279e3128fde5c3db5fe784b6fc00d4
- 5fc44bc2badb67648153759de5082a92f8ce9da9308dffc07f035dee0bece920
- 7bc281874a32bf4a364cf800826b62650d8c67efb15a088dd9d0295558043a71
- 7c5ad554bf6d496c57e4767efeb33dba75adc35771f0472f0cd32675f30b9abf
- 811e38165cb164768a901a92dae30f0e5570f90e9055a50a4b67a14f028bdb2c
- 821590fc905bf786438afa1e83eaf3c32d6411031d2c66e79fbd997ab9a7f37e
- 892657166b1192c61cfd9c84ff8e59e445f0a998f43bace122190d877a9aeb49
- 94b6da36c0fa409de9e8bb11fe7f0534b41da22798cbbfaad0814f463268fd5c
- b10073140d45a3488190b8600b67c651c6e3a8ca636ae7e52153bfd1649fb961
- dcdfca045b4aad4c0219463548cdba9619c221ee776e515446c775bf958e7362
- e435e8d490a36ac8f56cbfd931eca5504a6c6ba2c09fbd61a833b5ccbca4d14a
- fbf1961c71e5f892a8abd9d2dbc6c72e9b618bd96e05d64557f9acddcb1500bf
- fd0a8f8031ce65b74380e994d9a4c615fff62c1c889053896c6635842a089dc5
- fd4381d2d6a8140f1cd2bc19b661a4073e2540436ae287211955e439192f5e24
Coverage
Screenshots of Detection
ThreatGridUmbrella
Win.Dropper.Fareit-6680873-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\WINRAR
- Value Name: HWID
- <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9
- Value Name: F
- <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5
- Value Name: F
- <HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC
- Value Name: F
- 3749282D282E1E80C56CAE5A
- Stertorous8
- Decent5
- A4gds89g46dfgs
- Reserveful
- Sabbagh0
- Elfic
- 185[.]36[.]191[.]6
- 104[.]24[.]126[.]133
- www[.]bellyrocksh[.]com
- etete[.]eu
- larrydaves[.]cf
- vivsinomain1[.]cf
- sunnynaturelstone[.]com
- %AppData%\D282E1\1E80C5.lck
- %System32%\config\SAM
- %LocalAppData%\Temp\1153725803.bat
- 0d221abd5eaf60a723ae0e93866fe0cb6aaf2c23046c567427ba1bff0665c02e
- 18096cf4c75fc51a36b58e484848d2bdc39c426944a4f40b7b99592745bb5944
- 1b38f6fa030cea6692b79f688cbdf7cc0b09105cee0706a7f04a52d44ee36704
- 21458efd813e4c45d2bae2d8c6acca70ae748590b820387c3c7d68f98b8278ae
- 2f8cad659288c512b79db69fcac1628f52bfd3f7b60fe37835701186e67eac57
- 46bbaf619bdc28747cc62945e9caccc27d8848c0ab07c52918cad4290cc067c5
- 49f4e7e79ad9e6a2009286e0ab738f0e41abf82fd495ced8aca3387455f442c7
- 6076060229b2536037d85ca3050441b2a713a26b316d60a03347c8b380dce96c
- 753a70cf5cac5dbadd649cd30a25665267b174c2917c98ec0bb70919f610cc15
- 7a9bcdf5fd9edf0cd59e1d60cf3c31d7b0365f6b894170a9c56cea8f7f07d4bd
- 8408b21f4e141a7e94f3604f422e78baabeb30b7d1ea98a7f25bd4b4d75e7a1d
- 8ac3a9a28f34bcaeb7bae278b1f843c58dd9e8ab5c248c339a2deb779955d494
- 8dbf7b8ddffaafe6781321100351b769190a8e1dd4273a1d6b7660159857540e
- 9394988bb9d819321fb1febe7522e57a995eeb10b45716120eef7b7588bd51ac
- 998447cb9f7d5377be0cafd30b03a6b2f2f40e2860234abb6af08ef551d491f0
- ae2c150a838a6694c64ae712a964cbd086413b80ef427507b54957531c2aa6b4
- b34d4f5fe5e5b10cbc519634a0184d818d9ab20cf8107dfd4206793226b86319
- bb9010216f0dbe202446ea44d191a9e5a09f3bd23b453e13685063aa23ae1671
- c3cfeb64a23fca1da202e6e4837ef4a7eeabb6711d97a8e2c87130e3d47d7d66
- c56acb67efeb900524883c2268f05f27fa5fc549a3c15bb10639ca0634e8e037
- ecf51b788b7cd3bcb0d44802666ac24f8b9f6629159bb6fe1a9e70b68381c7a8
- ed43e191adf1a6f2af897f4d7a1eccd88aa11636dca56507d367c40f2732da76
Coverage
Screenshots of Detection
ThreatGridUmbrella